
Welcome Back to setting up a new computer!
So far we have spoke about the location of our new computer, and unpacking of our new computer.
The picture is what is called the rear computer panel. Keep in mind not all rear computer panels look the same, but generally they will all have similar parts that will be referred to as connectors, ports.
Some computers may have all the ports and connectors on the rear panel of their computer as pictured, and some not have as many ports and connectors. That’s fine!
When we are done YOU will be able to impress all your friends with your computer rear panel knowledge! How does that sound?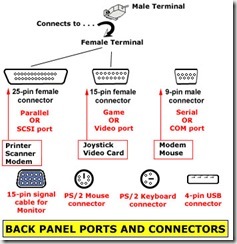
For Safety reasons, I do need to stress its ALWAYS a good idea to completely shut off your computer, and unplug it from its electrical source. We don’t want to get electric shocks or worse! You also will take the chance of damaging your computer as well, but personally? I think you are more important.
Keep in mind that connectors have male and female counterparts. The male has the pins while the female has the holes.
At this point we have NOTHING plugged in to the electrical outlet! It comes last! If you have anything plugged in? Unplug it!
As I’m sure you have guessed already the tower can be called, CPU, tower, system unit. This is the brains of the computer.
Peripheral Devices
Peripheral Devices are items we will plug into the CPU, Tower or system unit. Some examples of peripheral devices is the keyboard and mouse. Your monitor is almost like a TV screen, and you are reading these directions through a monitor. The speakers add sound, and of course our printer.
Scanners, joysticks, cameras, modem, etc are all peripheral devices.
Static Buildup
In our last lesson I mentioned that magnetics fields are NOT a computer’s friend. Today I wanted to mention neither is Static Buildup.
Do you remember as kids you dragged your feet along the carpet, and then touched your sibling to shock them? That can kill sensitive components of a computer. Most recommend placing the unit on a anti-static pad to prevent this.
I have to admit I’m bad at this. Normally, before handling anything? I touch something besides the computer parts. That releases the shock, and I move on. Carpeted areas are the worse for the shock and static. Others use anti static wrist pads, etc.
Setting up your new computer: Plug in those connections!
Note: Today’s technology tends to use what they call ‘wireless’ connection. It is exactly what it sounds like. There is no wires to plug into the CPU at all. Its amazing to watch once you turn on your computer that these Peripheral Devices connect automatically. Depending on your operating system peripheral software may or may not be needed. Normally, they will include it just in case. Your first clue will be if it NOT working after you boot up the computer, or the computer asks for the software. The newer computers normally will search out, and install the software on its own. These Peripheral Devices normally work on batteries: keyboard or mouse. Check your batteries to make sure they work if your computer isn’t responding.
Second Note: USB ports seem to be more popular to use for keyboards and mice. I will cover USB ports as well, but wanted to note this in case your computer isn’t using the traditional PS/2 port for those peripheral devices. (Don’t worry you will know what USB and PS/2 are soon!)
What is nice about computer’s today is that the manufacturers got smart, and started put pictures next to the connections. In the picture below you can see the green area that shows a mouse.
PS/2 Port
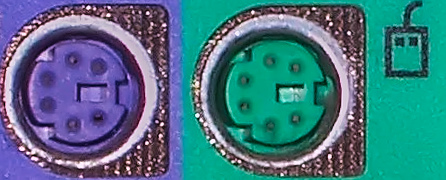
Pictured above is a PS/2 port on the back of your computer. This is the female connector that has holes. Notice the outside shape isn't a true circle, but has almost notch looking curves.  PS/2 Ports are normally used for the keyboard or mouse.
PS/2 Ports are normally used for the keyboard or mouse.
At times you will have check to see if you lined up the outside shape I mentioned above when you push them into the back of your computer. Green cord goes into the green connector, as does the purple goes in the purple. The cords would be the male connection!
These should slide in easily. Don’t force them, because you can break it.
USB Port

The UBS port that looks rather flat, and has that solid white portion on top. The cable you use is flat has well, and UBS normally just snap right in.
The USB ports don’t normally have anything labeled like they do above. You just grab a USB port that is available.
It seems to me technology is moving towards using more USB ports. You may have these on the front panel of the computer, rear panel of the computer, or both.
UBS ports are normally connected to items like: mouse, keyboard, speakers, printers, joysticks, headphones, etc.
I normally place mouse, keyboard, speakers, printers plugged into the back of my computer. On the front of my computer? I have our headphones and camera. We don’t use those all the time, and when we do use them we plug them in. Its an easier access to the ports for me. If they aren’t using them? They are in the drawer.
Ethernet
The Ethernet reminds me of an oversized phone cord plug. You know how you plug your phone cord into the jack?
If you have dial up you ma y not use this.
y not use this.
This normally is a connection that is used for high speed internet like DSL or cable.
One end would plug into the rear panel of the computer where pictured.
The other end of the cord would plug into your router or modem that your internet provider gave you – or had you buy.

The cords with the oversized phone connector plug (ethernet) is normally pretty thick and normally colored blue.
If you are using dial up internet connection? Please see two websites for insight. Dialup Modem one, Dialup Modem Two
Serial Ports – These it seems are being phrased out.
These are serial po rts. As you can see you will have to have a cord that is a female version. You also have to screws on the edge. Its for a more secure fit.
rts. As you can see you will have to have a cord that is a female version. You also have to screws on the edge. Its for a more secure fit.
Serial ports and Parallel Ports are similar, and to be honest seems to me are being phased out. They are being replaced by USB, or PS/2 ports
This is a  Parallel computer or what some call a printer port. This would be a good example of a male port.
Parallel computer or what some call a printer port. This would be a good example of a male port.
Some printer ports have a connectors may look this for this.

These ports are normally your very LONG ones!
This is the VGA port or video port, and is normally used for your monitor.

Audio Jacks
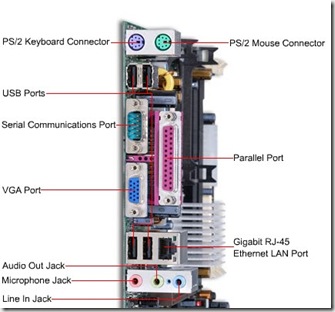
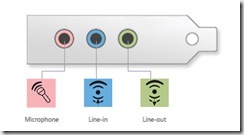
The above is all the jacks we have dealt with so far, but the ones on the bottom called audio jacks. As you can see these are normally colored coded to make it easy. These jacks directly connect to your computer's sound card or sound processor.
These can be used for your speakers, microphone or headset, or music players for example. We use them for the headset, because our family computer is in the living room. We don’t need to hear youtube, or games playing while watching television!
Most desktop computers have at least one line-in jack to connect a music player or other audio device and one line-out jack to connect speakers. These jacks typically appear on the back of a desktop computer. Many desktop computers also have a microphone jack, which is often on the front of the computer.
Power Port or Power Plug

This is the main electrical source plug from the back of your computer into your surge protector.
All the ports and connections aren’t that hard. Just need to find the spot that basically look like they go together pretty much. I know my children took scraps of paper, and wrote ‘printer’ or ‘monitor’ or what have you on each plug or cable and taped them on the cords or cables as they figured them out.
Remember to plug all your electrical plugs into your surge suppressor, and then plug that into your grounded outlet. Remind those from lesson 2?
According to most manufacturers that I have seen they ask you to turn on the monitor first, printer, speakers, etc – last but NOT least turn on your CPU or tower. During this portion of your computer setup it may take a while for it to bootup as they call it.
You may also get some startup questions and instructions. If some screens rush through before you can read them? Don’t worry to much about it. If they needed your input they would stop until you answered the question.
Well until next time this part of our step three of setting up your computer or setting your PC is complete.
 Just a single day after Google unveiled Google+, the company's brand new social networking service, Google decided it would be a good idea to open up the invitation process late Wednesday afternoon to all those fortunate enough to have already been invited to participate in the service.
Just a single day after Google unveiled Google+, the company's brand new social networking service, Google decided it would be a good idea to open up the invitation process late Wednesday afternoon to all those fortunate enough to have already been invited to participate in the service.





























 When it comes to the most powerful supercomputers in the world, I don't think it is to anybody's great surprise that the most powerful one is located in Japan. This new Japanese supercomputer has just recently earned the top spot among all the supercomputers in the world with a performance that makes other supercomputers look like a TI-82.
When it comes to the most powerful supercomputers in the world, I don't think it is to anybody's great surprise that the most powerful one is located in Japan. This new Japanese supercomputer has just recently earned the top spot among all the supercomputers in the world with a performance that makes other supercomputers look like a TI-82.
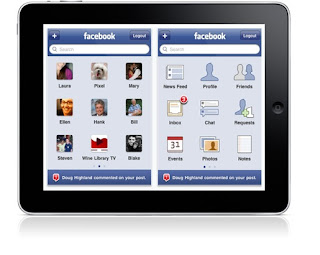 Facebook is planning on releasing an app for the iPad in the next couple of weeks that is said to feature a "slick design" as well as new Facebook Chat and Groups functionality. In addition to that, the app is also said to feature an "amazing" photo and video experience.
Facebook is planning on releasing an app for the iPad in the next couple of weeks that is said to feature a "slick design" as well as new Facebook Chat and Groups functionality. In addition to that, the app is also said to feature an "amazing" photo and video experience. Put your eye on the problem with
Put your eye on the problem with  Samsung has just recently introduced 30-nanometer-class1 DDR3 synchronous dynamic random access memory (DRAM) modules designed for upgrading your PC. This new generation of faster, energy efficient DRAM modules is going to be available via consumer retail channels this summer.
Samsung has just recently introduced 30-nanometer-class1 DDR3 synchronous dynamic random access memory (DRAM) modules designed for upgrading your PC. This new generation of faster, energy efficient DRAM modules is going to be available via consumer retail channels this summer.





 Find out what is going on in the
Find out what is going on in the 